According to Microsoft:
The Automatic Root Certificates Update component is designed to automatically check the list of trusted authorities on the Microsoft Windows Update Web site. Specifically, there is a list of trusted root certification authorities (CAs) stored on the local computer. When an application is presented with a certificate issued by a CA, it will check the local copy of the trusted root CA list. If the certificate is not in the list, the Automatic Root Certificates Update component will contact the Microsoft Windows Update Web site to see if an update is available. If the CA has been added to the Microsoft list of trusted CAs, its certificate will automatically be added to the trusted certificate store on the computer. Automatic Roots Certificate Update Configuration
This of course can add additional time to web browsing and depending on WIndows Services, GPO configuration and connectivity may not be possible for a user to complete. Therefore it is advisable to update the Trusted Roots Certificate Store reguarly as part of your VDA Master Image maintenance routine using the following commands that may be run from a Powershell console.
# Create C:\temp\certs
md C:\temp\certs
# download latest SST from Microsoft
CertUtil –generateSSTFromWU C:\temp\certs\RootStore.sst
# Import RootStore.sst to Trusted Root CA Store
$file=Get-ChildItem -Path C:\temp\certs\Rootstore.sst
$file | Import-Certificate -CertStoreLocation Cert:\LocalMachine\Root\
After completing this procedure, the Trusted Roots Certificate Store will contain well over 350 CA root certificates.
Configure Trusted Roots and Disallowed Certificates
An update is available that enables administrators to update trusted and disallowed CTLs in disconnected environments in Windows
UPDATE!!!!!!
An issue has been discovered whereby updating the Microsoft Root Certificate Authority trusted root certificate can prevent the installation of certain device drivers.
e.g. While installing the Citrix WorkSpace App (including the USB redirection driver), the following error occurs and the driver is not deployed.
Error - CComponentManager::GetInstallStatus(600) - Installation NOT successful for 'USB', error: 1603.
This also results in a number of the WorkSpace App components not being deployed as the installation routine terminates prematurely.
This issue may affect other drivers that are digitally signed. In the example above, the USB cat files supplied by Citrix are signed by the following certificate chain.
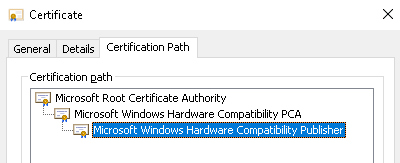
Although all appears normal and correct (certs are present and trusted), the Citrix USB driver fails to install when the Microsoft certificates have been updated.
To avoid this problem, run
CertUtil –generateSSTFromWU C:\temp\certs\RootStore.sst
to generate the SST file.
Open the SST file and select all certificates except for Microsoft certificates.
While holding down CTRL, export the list of certificates to a new SST file (RootStore2.sst)
Then import the modified SST file
$file=Get-ChildItem -Path C:\temp\certs\Rootstore2.sst
$file | Import-Certificate -CertStoreLocation Cert:\LocalMachine\Root\ |
